Intro
Some time ago, I was in the role of a consultant on how to enable Device Guard in an enterprise in a step-by-step manner. That was the Windows 10 OS, and enabling Credential Guard is another layer of protection against various types of attacks that aim to steal your credentials, such as NTLM hashes, typically with tools like Mimikatz.
The approach was chosen when we enabled Credentials Guards in a granular manner, avoiding potential issues with laptop botting, as many of the company’s employees were working remotely at this moment
Enabling Credentials Guard
We used the original Microsoft DG_Readiness_Tool_v3.6.ps1 tool.
If we just execute
powershell -f DG_Readiness_Tool_v3.6.ps1 -cap
we get
C:\projects\DeviceGuard\dgreadiness_v3.6>powershell -f DG_Readiness_Tool_v3.6.ps1 -cap
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/19/2021 12:46 PM DGLogs
###########################################################################
Readiness Tool Version 3.4 Release.
Tool to check if your device is capable to run Device Guard and Credential Guard.
###########################################################################
###########################################################################
OS and Hardware requirements for enabling Device Guard and Credential Guard
1. OS SKUs: Available only on these OS Skus - Enterprise, Server, Education, Enterprise IoT, Pro, and Home
2. Hardware: Recent hardware that supports virtualization extension with SLAT
To learn more please visit: https://aka.ms/dgwhcr
###########################################################################
Checking if the device is DG/CG Capable
====================== Step 1 Driver Compat ======================
Enabling Driver verifier
Verifier Flags: 0x02001000
Standard Flags:
[ ] 0x00000001 Special pool.
[ ] 0x00000002 Force IRQL checking.
[ ] 0x00000008 Pool tracking.
[ ] 0x00000010 I/O verification.
[ ] 0x00000020 Deadlock detection.
[ ] 0x00000080 DMA checking.
[ ] 0x00000100 Security checks.
[ ] 0x00000800 Miscellaneous checks.
[ ] 0x00020000 DDI compliance checking.
Additional Flags:
[ ] 0x00000004 Randomized low resources simulation.
[ ] 0x00000200 Force pending I/O requests.
[ ] 0x00000400 IRP logging.
[ ] 0x00002000 Invariant MDL checking for stack. [ ] 0x00004000 Invariant MDL checking for driver. [ ] 0x00008000 Power framework delay fuzzing. [ ] 0x00010000 Port/miniport interface checking. 12:48 PM [ ] 0x00040000 Systematic low resources simulation. [ ] 0x00080000 DDI compliance checking (additional). [ ] 0x00200000 NDIS/WIFI verification. [ ] 0x00800000 Kernel synchronization delay fuzzing. [ ] 0x01000000 VM switch verification. [X] 0x02000000 Code integrity checks. Internal Flags: [X] 0x00001000 Additional debug information. [X] Indicates flag is enabled. Advanced Options: Log Only Code Integrity Statistics Boot Mode: Persistent Rules: All rules are using default settings Verified Drivers: All Drivers The system reboot is required for the changes to take effect. Enabling Driver Verifier and Rebooting system Please re-execute this script after reboot.... Please reboot manually and run the script again....
Two notes here. It is not true that DeviceGuard is available only on Enterprise editions of the Windows OS, and it runs Driver Verifier, a special utility used by kernel code developers for testing their drivers. The enabled flags are:
- 0x02000000 — Code Integrity Checks. This enables verification of driver code integrity, checking for tampering or corruption of driver binaries. It ensures the code hasn’t been modified in memory and that it conforms to expected standards.
- 0x00001000 — Additional Debug Information. Provides enhanced debugging output for use with debugging tools like WinDbg. It can help you track down bugs more effectively by including extra diagnostics.
The first flag can cause crashes when loading some drivers that may not be compatible with “Code Integrity”
I had problems with OS loading, and that was fixed automatically with OS restoring mechanism when it detects that OS can be loaded and restores drivers configuration from the special registry path.
You can verify for loading problems with
verifier.exe /flags 0x02000000 /all /log.code_integrity
Run
powershell -f DG_Readiness_Tool_v3.6.ps1 -cap -cg
and secureboot was not enabled in the configuration
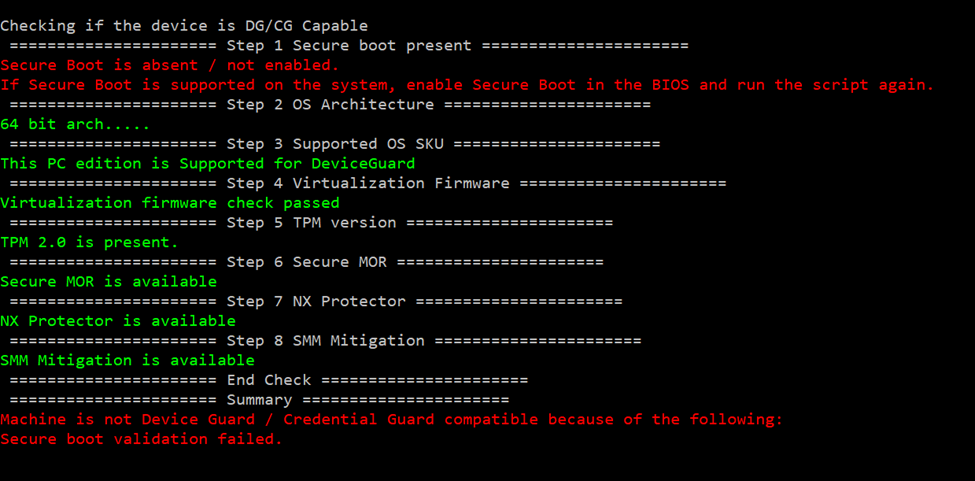
Enabling of secure boot depends on your laptop manufacturer on my HP laptop, it looked like this
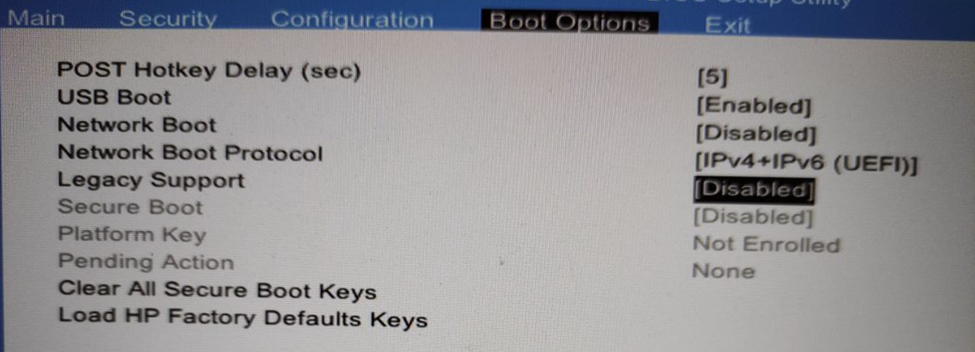
just select Load HP factory defaults keys
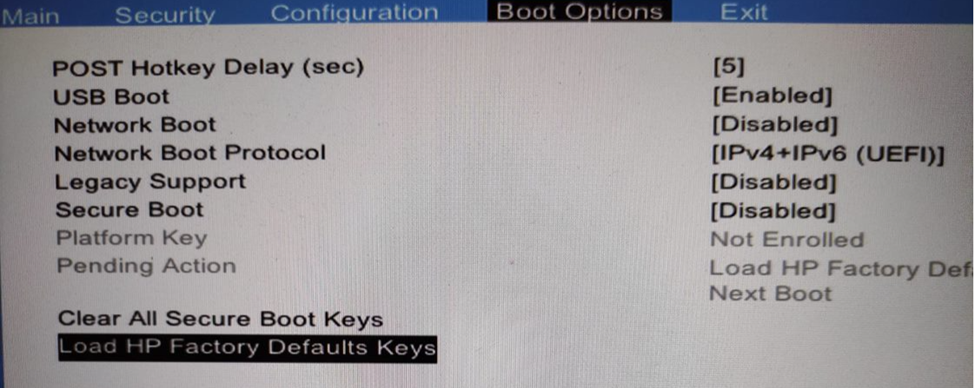
and configure secure boot to enable
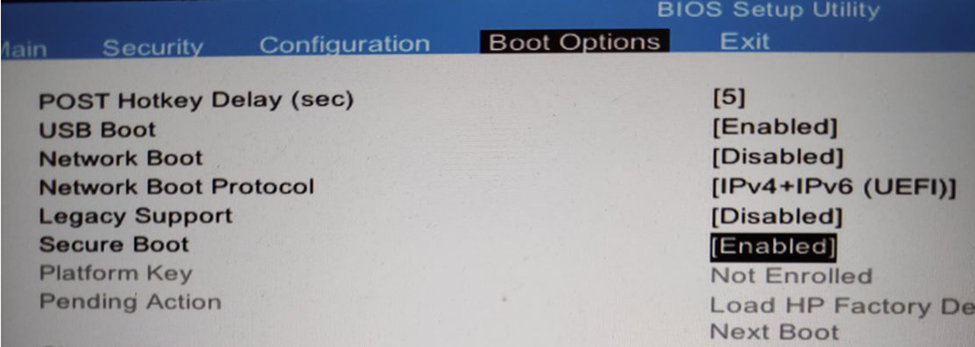
Enabled Secure Boot will mean a slight increase in boot time, as cryptographic operations related to signature verification on firmware and images will be performed during the process, preventing the loading of malicious code.
After botting, re-run again
powershell -f DG_Readiness_Tool_v3.6.ps1 -cap -cg
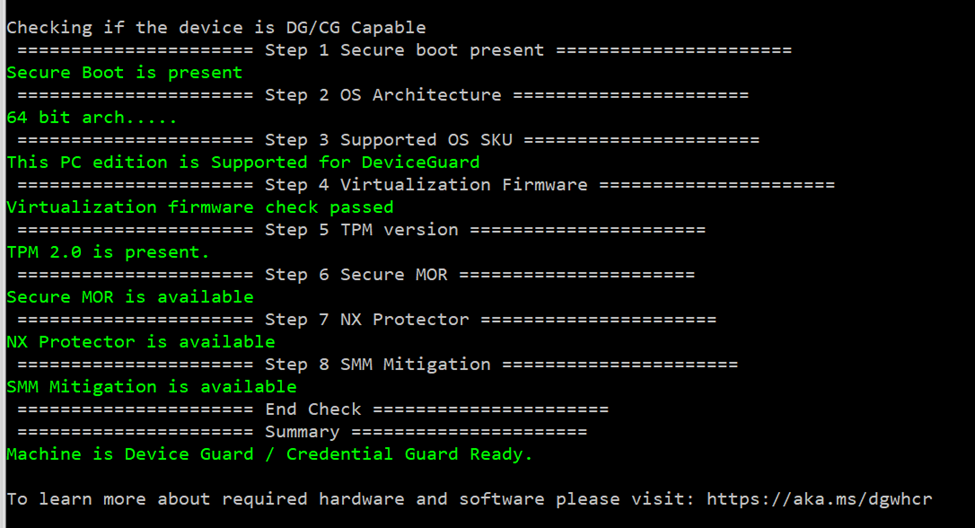
Now it’s possible to run Enable for Credential Guard only.
It’s important to pay attention to the supported arguments of the cmdlet:param([switch]$Capable, [switch]$Ready, [switch]$Enable, [switch]$Disable, $SIPolicyPath, [switch]$AutoReboot, [switch]$DG, [switch]$CG, [switch]$HVCI, [switch]$HLK, [switch]$Clear, [switch]$ResetVerifier)
and use them accordingly.
The point is that when we previously ran:powershell -f DG_Readiness_Tool_v3.6.ps1 -cap
it also triggered a check for Device Guard compatibility, which launched the Verifier to inspect kernel-mode drivers—this could lead to the system being unable to boot.
If we only want to check whether Credential Guard can be enabled, we should run:powershell -f DG_Readiness_Tool_v3.6.ps1 -cap -cg
If we test dumping hashes without credential guard we will get with mimikatz
sekurlsa::logonpasswords
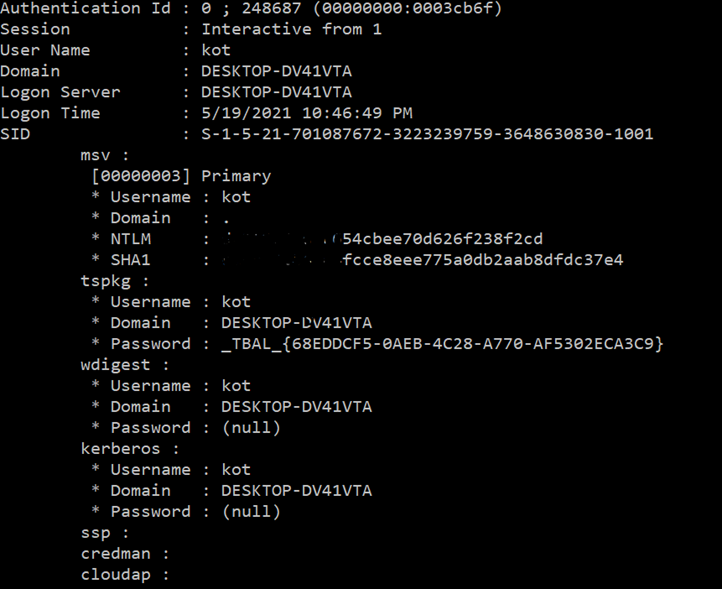
That weak NTLM hash can be used for the pass-to-hash attacks as well as for brute forcing it to get the plaintext password. With mimikatz we could even get the original plain text password in case of using a not secure, weak provider like wdigest.
Enable credentials guard
powershell -f DG_Readiness_Tool_v3.6.ps1 -enable -cg
and reboot the laptop
powershell -f DG_Readiness_Tool_v3.6.ps1 -ready -cg
will give us
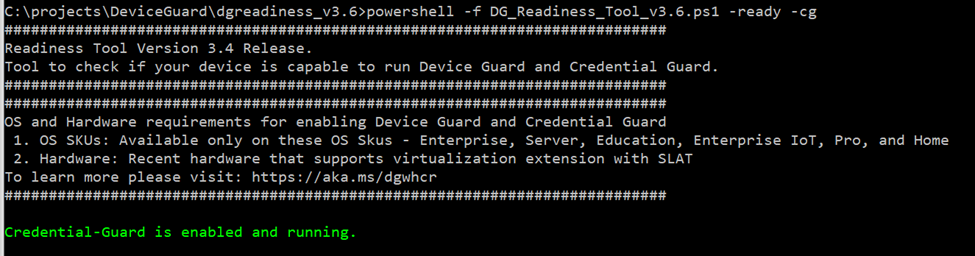
The main idea of enabling device guard is to do it step by step, starting from credentials guard

And we have to enable Hyper-V for this, which is one of the prerequisites.
After enabling Credentials Guard mimikatz doesn’t work
privilege::debug
sekurlsa::logonPasswords
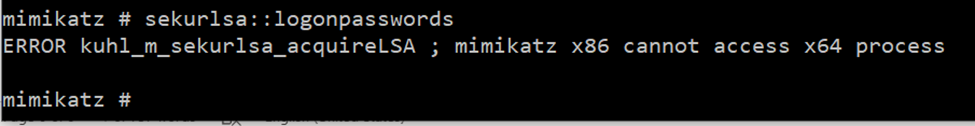
Access to the LSASS process address space is no longer possible; we also see a new process, LsaIso (Lsa Isolated).
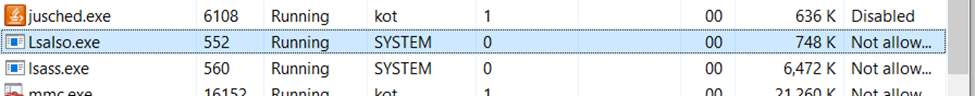
To disable credentials guard, just execute
powershell -f DG_Readiness_Tool_v3.6.ps1 -disable -cg
References
Support for Device Guard and Credential Guard on Windows 10 with McAfee encryption products